Services d’infrastructure
Contenu en cours de développement
Objectifs de certification
RHCE EX300
- System configuration and management
- 1.1. Use network teaming or bonding to configure aggregated network links between two Red Hat Enterprise Linux systems.
- 1.2. Configure IPv6 addresses and perform basic IPv6 troubleshooting.
- 1.3. Route IP traffic and create static routes.
- 1.4. Use firewalld and associated mechanisms such as rich rules, zones and custom rules, to implement packet filtering and configure network address translation (NAT).
- 1.5. Use /proc/sys and sysctl to modify and set kernel runtime parameters.
- DNS
- 4.1. Configure a caching-only name server.
- 4.2. Troubleshoot DNS client issues.
- NTP
- 9.1. Synchronize time using other NTP peers.
LPIC 2
- Sujet 207 : Serveur de nom de domaine
- 207.1 Configuration de base d’un serveur DNS (valeur : 3)
- 207.2 Création et mise à jour des zones DNS (valeur : 3)
- 207.3 Sécurisation d’un serveur DNS (valeur : 2)
- Sujet 210 : Gestion des clients réseau
- 210.1 Configuration DHCP (valeur : 2)
1. Protocoles et logiciels d’infrastructure
Adaptez les pare-feux !
1.1. Synchronisation dans le temps
NTP
- Client/Serveur à protéger des tentatives de connexions vers le serveur et de tentatives de configuration
- UDP 123 (Bien que NTP soit le plus souvent utilisé avec UDP, il peut aussi l’être avec TCP.)
- Vulnérabilités / sécurité NTP
- Nécessaire pour l’usage des protocoles sécurisés, des authentifications, la légalité des logs, les protocoles en temps réel et de synchronisation de bases de données.
- SNTP
- Projet NTP Pool : http://www.pool.ntp.org/fr/
Network Time Protocol (« protocole d’heure réseau ») ou NTP est un protocole qui permet de synchroniser, via un réseau informatique, l’horloge locale d’ordinateurs sur une référence d’heure. Le projet NTP propose une solution globale et universelle de synchronisation qui est utilisable dans le monde entier.
La version 3 de NTP est la plus répandue à ce jour. Elle est formalisée par la RFC 1305 qui spécifie plusieurs aspects :
- la description du protocole réseau (Architecture)
- les modes de fonctionnement (Messages)
- les algorithmes à mettre en place dans les machines.
La version 4 de NTP est une révision importante publiée dans la RFC 5905 en juin 2010.
Aussitôt après la parution de la version 3 de NTP, une version simplifiée est apparue, appelée « Simple Network Time Protocol » (SNTP) qui a également fait l’objet de plusieurs RFC. Par rapport à NTP, cette version est simplifiée dans le sens qu’elle ne spécifie pas les algorithmes à mettre en place dans les machines.
Source : manquante.
1.2. Configuration dynamique IPv4
DHCP
- UDP 67 (Serveur) / UDP 68 (Client)
Déploiements :
- Serveur(s) DHCP
- DHCP Relay
1.3. Protocoles IPv6 IPAM
IPAM signifie IP Adresses management et correspond à des solutions de planification, de gestion et de contrôle des adresses IP utilisée et distribuées au sein de réseaux maîtrisés (Les centres de données, les environnements virtualisés, …). Ce type solution peut aider à la transition IPv6 et peut faire jouer les protocoles envisagés dans ce chapitre (DNS, DHCP, etc.).
Ici on parlera de :
- Neighbor Discovery ND ICMPv6
Les “Router Adverisements” (RA) annoncent le routeur lui-même comme passerelle ainsi que la méthode de configuration que les hôtes du réseau utilisent, le préfixe utilisé pour l’autoconfiguration automatique sans état (SLAAC), le serveur DNS à utiliser, etc.
- DHCPv6
Nouvelle version réécrite pour IPv6.
- UDP 547 (Serveur) / UDP 546 (Client)
- Stateful
- Stateless
1.4 Auto-configuration automatique sans état (SLAAC)
Questions techniques
La gestion d’un réseau IPv6 pose plusieurs questions techniques :
- Comment distribuer un préfixe global ?
- Comment distribuer des options telles que le résolveur de noms (DNS) IPv6 ?
- Quand et comment utiliser l’adressage Unique Local (ULA) privé ?
- Comment identifier le trafic de gestion et profiter du multicast ?
- Comment re-numéroter de sites en IPv6 ?
- Que choisir ? L’auto-configuration automatique ou DHCPv6 ?
- Comment fonctionne SLAAC ?
Topologies et constructeurs
Les solutions de gestion d’adressage IPv6 se déploient selon les profils et les topologies :
- SME/PME, SOHO ou accès public
- Entreprise mono-site
- Entreprise Multi-site, core, data-center, branch office
- Core Internet, FAI, Gros fournisseurs de services
- Mais aussi selon les constructeurs choisis (en fonction de leur support d’IPv6) :
- Cisco, …
- Microsoft, …
- VMWare, …
- Les services Cloud
Le routeur configure le réseau
Une nouveauté d’IPv6 parmi d’autres sont les échanges Neighbor Discovery (ND) “Router Solicitation” (RS ICMPv6 type 133) et “Router Advertisement” (RA ICMPv6 type 134).
Ces paquets configurent le réseau en fournissant sur demande ou en annonce gratuite les paramètres de configuration des interfaces.
Paramètres RA
Les Router Advertisements sont des messages ICMPv6 type 134 disposant d’un en-tête IPv6 et d’un en-tête de couche 2 (Ethernet par exemple).
Ces paquets contiennent principalement, a priori,
- un champ de drapeaux (Flags) qui indique l’usage de DHCP stateful et/ou stateless
- et une valeur de préférence de routeur,
- des options :
- Un préfixe avec son masque
- Le MTU que l’interface doit prendre
- L’adresse source de couche 2 du message
- Éventuellement, l’adresse d’un serveur DNS récursif, un cache (RDNSS). Cette option est peu supportée.
Router Advertisements
- Type 134, code 0
- Drapeaux M, O, Prf
- Options : MTU, adresse source L2 et préfixe
- L’adresse source du message DOIT être l’adresse Link-Local de l’interface qui envoie le message
- L’adresse de destination est habituellement l’adresse source du routeur sollicité (Router Solicitation) ou l’adresse All-Nodes Multicast (
FF02::1)
0 1 2 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Type | Code | Checksum |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Cur Hop Limit |M|O|H|Prf|Resvd| Router Lifetime |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Reachable Time |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Retrans Timer |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Options ...
+-+-+-+-+-+-+-+-+-+-+-+-
RFC4191 màj Neighbor Discovery RFC 4861 Section 4.2 et RFC 6275 Section 7.1
RA : Flags et Options
Ethernet II, Src: Globalsc_01:df:95 (f0:ad:4e:01:df:95), Dst: IPv6mcast_00:00:00:01 (33:33:00:00:00:01)
Internet Protocol Version 6, Src: fe80::f2ad:4eff:fe01:df95 (fe80::f2ad:4eff:fe01:df95), Dst: ff02::1 (ff02::1)
Internet Control Message Protocol v6
Type: Router Advertisement (134)
Code: 0
Checksum: 0x1bc0 [correct]
Cur hop limit: 64
Flags: 0xc0
Router lifetime (s): 1800
Reachable time (ms): 0
Retrans timer (ms): 0
ICMPv6 Option (Prefix information : 2001:db8:ffff::/64)
ICMPv6 Option (MTU : 1500)
ICMPv6 Option (Source link-layer address : f0:ad:4e:01:df:95)
ICMPv6 Option (Recursive DNS Server fe80::f2ad:4eff:fe01:df95)
Quatre méthodes de configuration IPv6
Ces quatre méthodes peuvent se combiner au choix et servir à la gestion de l’adressage IPv6 ainsi qu’à la re-numérotation IPv6. Elles sont indiquées dans le champs Flags :
- Managed address configuration: Flag M : DHCPv6 Stateful assignation d’adresse dynamique
- Other configuration : Flag O :DHCPv6 Stateless demande d’options supplémentaires
- Home Agent: Mobilité IPv6
- Prf (Default Router Preference): valorisation du RA par rapport à un autre (3 valeurs, 2 bits)
- Reserved: Pour un usage futur
| . | Configuration | Flag M | Flag O |
|---|---|---|---|
| 1) | Configuration statique | 0 | 0 |
| 2) | Stateless Automatic Autoconfiguration (SLAAC) seul | 0 | 0 |
| 3) | DHCPv6 (Stateful) | 1 | 1 |
| 4) | DHCPv6 Stateless | 0 | 1 |
Option Prefix Information
L’option Prefix Information liste chaque préfixe IPv6 annoncé avec une série d’informations :
- Le drapeau “L” “on-link” (OnLinkFlag).
- La valeur de durée de vie de validité
- Le drapeau “A” “Autonomous address configuration” qui indique que l’interface utilise SLAAC avec ce préfixe.
- La valeur de durée de vie de préférée
Exemple Option Type 3
Quel que soit la position du drapaux M ou O, ce sont les champs L et A qui indiquent l’usage de l’autoconfiguration automatique sans état (SLAAC).
Cela signifie qu’une interface pourrait disposer pour chaque préfixe annoncé d’une adresse attribuée par DHCPv6 et une ou plusieurs adresses SLAAC.
ICMPv6 Option (Prefix information : 2001:db8:ffff::/64)
Type: Prefix information (3)
Length: 4 (32 bytes)
Prefix Length: 64
Flag: 0xc0
1... .... = On-link flag(L): Set
.1.. .... = Autonomous address-configuration flag(A): Set
..0. .... = Router address flag(R): Not set
...0 0000 = Reserved: 0
Valid Lifetime: 3600
Preferred Lifetime: 3600
Reserved
Prefix: 2001:db8:ffff:: (2001:db8:ffff::)
Scénarios RA
Flags :
| x | SLAAC Autonomous (option Prefix Information) | Managed Configuration Address ManagedFlag | Other Configuration OtherConfigFlag | Scénario |
| 1 SLAAC | 1 | 0 | 0 | Assignation : sans état, Passerelle : sans état, DNS : RDNSS ou autre |
| 2. Stateless DHCPv6 | 1 | 0 | 1 | Assignation : sans état, Passerelle : sans état, DNS : DHCPv6 |
| 3 Statefull DHCPv6 | 0 | 1 | 1 | Assignation : DHCPv6, Passerelle : sans état, DNS : DHCPv6 |
| 3 Statefull DHCPv6 + SLAAC | 1 | 1 | 1 | Assignation : DHCPv6 + SLAAC, Passerelle : sans état, DNS : DHCPv6 |
Le champs Prf donne une préférence au routeur codée sur 2 bits : 01(High), 00 (Medium par default), 11 (Low).
L’auto-configuration automatique sans état (SLAAC)
L’autoconfiguration sans état, Stateless Automatic Auto Configuration (SLAAC) :
- Méthode par défaut dans un environnement routé pour les routeurs et les noeuds.
- Le routeur (RAs) donne toute une série de paramètres :
- préfixe(s) avec le Flag A activé, mtu, préférence, passerelle, Flags M et O
- L’interface construit elle-même son identifiant d’interface selon différentes méthodes
- MAC EUI 64
- de manière aléaloire
Illustration du mécanisme SLAAC
- Toute interface activée en IPv6 génère une adresse Lien Local avec le préfixe FE80::/10 suivi d’un identifiant d’interface.
- Elle vérifie l’existence de l’adresse générée via un mécanisme appelé DAD (Duplicate Address Detection).
- Sans réponse, elle peut utiliser cette adresse sur le lien local.
- Elle sollicite un routeur en multicast.
- S’il est présent sur le réseau, le routeur IPv6 répond avec des paramètres de configuration RA et Options.
- L’interface élabore son ou ses adresses selon ce qu’indique le routeur. Elle installe sa passerelle par défaut.
- Régulièrement, l’interface va vérifier l’existence des noeuds voisins appris par processus ND (NUD).

SLAAC : adresses générées
Avec des RA dont les drapeaux sont placés M=1, O=1, L=1 et A=1 (sur le préfixe), cette interface pourra prendre quatre adresses, soit une DHCPv6, deux SLAAC et une Link-Local :
… (à compléter)
et ses trois groupes Multicast joints
… (à compléter)
1.5. DHCPv6
DHCPv6 est un nouveau protocole. Il utilise le port UDP numéro 546 sur les clients et le port UDP numéro 547 sur les serveurs.
Une interface contacte un serveur DHCPv6 avec l’adresse Multicast FF02::1:2. DHCPv6 utilise les adresses Link-Local (FE80::/10) :
- Le serveur assigne le préfixe et l’identifiant d’interface et des paramètres optionnels (DHCPv6 Stateful) : RFC 3315
- Le serveur assigne seulement des paramètres optionnels (DHCPv6 Stateless) : RFC 3736
- Le serveur délègue l’assignation d’un préfixe (DHCPv6 Prefix Delegation) : RFC 6603 (pas traité ici)
- Fonctionnalité DHCP Relay (pas traité ici)
DHCPv6 et RA
Dans tous les cas c’est le routeur qui prend en charge le trafic vers l’internet, automatiquement grâce aux annonces de passerelles embarquées dans les RA.
Les flags Managed et Other et autres paramètres sont gérés et configurées à partir du routeur !
Il est inutile de chercher le paramètre de la passerelle par défaut dans les services DHCPv6 à déployer.
DHCPv6 Stateless
DHCPv6 Stateless est un mode DHCPv6 sans état :
- utilise des messages Information-request/Reply
- ne fournit que des informations optionnelles : serveur DNS, NTP, SIP, etc.
- ne donne aucune adresse, elles sont générées par SLAAC ou attribuées
- ne maintient aucun état dynamique des clients qui le sollicitent
- Le RA flags sont notés M=0/1 et O=1 selon le déploiement choisi
DHCPv6 mode Stateful
Le serveur assigne l’adresse complète et des paramètres optionnels (Flags RA M=1 et O=1)
Ce mode est appelé DHCPv6 Stateful. Il est similaire à ce que DHCP IPv4 peut utilement fournir sur un réseau administré.
Le serveur maintient une base de données des liens (des baux).
En quatre message :
- Solicit
- Advertise
- Request
- Reply
ou deux messages (rapid commit) :
- Solicit
- Reply
Par exemple, en admettant que l’adresse lien-local du serveur est fe80::0011:22ff:fe33:5566/64 et que l’adresse lien-local du client est fe80::aabb:ccff:fedd:eeff/64,
- le client DHCPv6 envoie un Solicit de [
fe80::aabb:ccff:fedd:eeff]:546 à [ff02::1:2]:547. - le serveur DHCPv6 répond avec un Advertise (annonce) de [
fe80::0011:22ff:fe33:5566]:547 à [fe80::aabb:ccff:fedd:eeff]:546. - le client DHCPv6 répond avec un Request de [
fe80::aabb:ccff:fedd:eeff]:546 à [ff02::1:2]:547. - le serveur DHCPv6 termine avec un Reply de [
fe80::0011:22ff:fe33:5566]:547 à [fe80::aabb:ccff:fedd:eeff]:546.
DUID (DHCPv6 Unique Identifier)
Selon la section 9 du RFC 3315, les serveurs DHCP utilisent les DUIDs pour identifier les clients dans la sélection de paramètres et dans la sélection de son IA. Un IA (Identity Association) est une collection d’adresses assignés au client.
Le DUID doit être unique dans l’environnement et il est créé par le client. Parce que certains périphériques ne peuvent pas garder en mémoire cette information, il y a trois moyens de générer un DUID :
- L’adresse de couche 2 + horodatage
- “Vendor-assigned unique ID” basé sur un “Enterprise Number”
- L’adresse de couche 2
Cette nouvelle fonctionnalité vise notamment à identifier autrement que par une adresse MAC un client DHCPv6.
Messages DHCPv6
- 1- SOLICIT
- 2- ADVERTISE
- 3- REQUEST
- CONFIRM
- RENEW
- REBIND
- 4- REPLY
- RELEASE
- DECLINE
- RECONFIGURE
- 1- INFORMATION-REQUEST
- RELAY-FORW
- RELAY-REPL
DHCPv6 Conclusion
DHCPv6 est un outil puissant de configuration du réseau, conçu pour des topologies très larges :
- combiné au SLAAC
- DHCP relay
- Délégation de préfixe
Pour une discussion complémentaire sur DHCPv6 : http://ipv6friday.org/blog/2011/12/dhcpv6/
1.6. Résolution de noms
DNS
- UDP/TCP 53
- Vérifier le transfert
On ira relire utilement les chapitres du document :
Déploiements :
- Serveur Master/Slave pour une zone
- Serveur Resolver (cache)
- Serveur Forwarding (proxy)
- Serveur Split
- Serveur View Based
1.7. Logiciels
Logiciels standards
- Dnsmasq (DNS, DHCP, SLAAC, DHCPv6)
- RADVD (SLAAC)
- ISC-DHCP-Server (DHCP, DHCPv6)
- Bind9 (DNS)
- NTP (NTP)
- Chrony (NTP)
Surveillance
- ndpmon
- arpwatch
- PacketFence (NAC)
Logiciels IPAM
En Open Source, on trouvera une liste très active en la matière (https://en.wikipedia.org/wiki/IP_address_management). Il y a un véritable marché qui cible toute entreprise qui gère un centre de données. Chacun de ces logiciels peut être comparé à un autre en termes de fonctionnalités nécessaires (requirements).
2. Dnsmasq
Dnsmasq est un service léger qui offre les services DHCP, SLAAC, DHCPv6 et cache DNS. http://www.thekelleys.org.uk/dnsmasq/doc.html
Il s’installe via la commande :
yum -y install dnsmasq
La topologie du lab101 peut nous aider à déployer aisément et pédagogiquement tous ces services.
[root@r101 ~]# egrep -v "^#|^$" /etc/dnsmasq.conf
conf-dir=/etc/dnsmasq.d
[root@r101 ~]# egrep -v "^#|^$" /etc/dnsmasq.d/eth0.conf
dhcp-range=192.168.168.50,192.168.168.150,255.255.255.0,12h
dhcp-option=3,192.168.168.1
dhcp-range=fd00:168:168::2,fd00:168:168::500,slaac
[root@pc1-101 ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 52:54:00:7b:f3:1e brd ff:ff:ff:ff:ff:ff
inet 192.168.168.107/24 brd 192.168.168.255 scope global dynamic eth0
valid_lft 43120sec preferred_lft 43120sec
inet6 fd00:168:168::1b4/128 scope global dynamic
valid_lft 3523sec preferred_lft 3523sec
inet6 fd00:168:168:0:5054:ff:fe7b:f31e/64 scope global noprefixroute dynamic
valid_lft 3523sec preferred_lft 3523sec
inet6 fe80::5054:ff:fe7b:f31e/64 scope link
valid_lft forever preferred_lft forever
[root@pc1-101 ~]# cat /etc/resolv.conf
# Generated by NetworkManager
nameserver 192.168.168.1
nameserver fd00:168:168::1
[root@c1-101 ~]# ip -6 m
1: lo
inet6 ff02::1
inet6 ff01::1
2: eth0
inet6 ff02::1:ff00:1b4
inet6 ff02::1:ff7b:f31e users 2
inet6 ff02::1
inet6 ff01::1
Sur [root@r101 ~]#
nmcli c mod "System eth0" ipv6.address 2001:db8:168:168::1/64
nmcli c up "System eth0"
echo 'IPV6ADDR_SECONDARIES="2001:db8:168:168::1/64"' >> /etc/sysconfig/network-scripts/ifcfg-eth0
echo "dhcp-range=2001:db8:168:168::2,2001:db8:168:168::500,slaac" >> /etc/dnsmasq.d/eth0.conf
systemctl restart dnsmasq
[root@pc1-101 ~]# ip -6 a show eth0
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 fd00:168:168::1b4/128 scope global dynamic
valid_lft 3412sec preferred_lft 3412sec
inet6 fd00:168:168:0:5054:ff:fe7b:f31e/64 scope global noprefixroute dynamic
valid_lft 3412sec preferred_lft 3412sec
inet6 2001:db8:168:168:5054:ff:fe7b:f31e/64 scope global noprefixroute dynamic
valid_lft 3412sec preferred_lft 3412sec
inet6 fe80::5054:ff:fe7b:f31e/64 scope link
valid_lft forever preferred_lft forever
[root@pc1-101 ~]# ip -6 route
unreachable ::/96 dev lo metric 1024 error -113
unreachable ::ffff:0.0.0.0/96 dev lo metric 1024 error -113
2001:db8:168:168::/64 dev eth0 proto ra metric 100
unreachable 2002:a00::/24 dev lo metric 1024 error -113
unreachable 2002:7f00::/24 dev lo metric 1024 error -113
unreachable 2002:a9fe::/32 dev lo metric 1024 error -113
unreachable 2002:ac10::/28 dev lo metric 1024 error -113
unreachable 2002:c0a8::/32 dev lo metric 1024 error -113
unreachable 2002:e000::/19 dev lo metric 1024 error -113
unreachable 3ffe:ffff::/32 dev lo metric 1024 error -113
fd00:168:168::1b4 dev eth0 proto kernel metric 256 expires 3355sec
fd00:168:168::/64 dev eth0 proto ra metric 100
fe80::5054:ff:fefa:ad5f dev eth0 proto static metric 100
fe80::/64 dev eth0 proto kernel metric 256
default via fe80::5054:ff:fefa:ad5f dev eth0 proto static metric 100
default via fe80::5054:ff:fefa:ad5f dev eth0 proto static metric 100
[root@pc1-101 ~]# ping6 -c 1 2001:4860:4860::8888
PING 2001:4860:4860::8888(2001:4860:4860::8888) 56 data bytes
From 2001:db8:168:168::1 icmp_seq=1 Destination unreachable: No route
--- 2001:4860:4860::8888 ping statistics ---
1 packets transmitted, 0 received, +1 errors, 100% packet loss, time 0ms
From 2001:db8:168:168::1 icmp_seq=1 Destination unreachable: No route
[root@pc1-101 ~]# wget http://www.google.com
--2017-03-13 23:25:02-- http://www.google.com/
Resolving www.google.com (www.google.com)... 2a00:1450:4007:810::2004, 216.58.209.228
Connecting to www.google.com (www.google.com)|2a00:1450:4007:810::2004|:80... failed: Network is unreachable.
Connecting to www.google.com (www.google.com)|216.58.209.228|:80... connected.
HTTP request sent, awaiting response... 302 Found
Location: http://www.google.fr/?gfe_rd=cr&ei=PhzHWIDrE8bS8AfF0rngBg [following]
--2017-03-13 23:25:02-- http://www.google.fr/?gfe_rd=cr&ei=PhzHWIDrE8bS8AfF0rngBg
Resolving www.google.fr (www.google.fr)... 2a00:1450:4007:80f::2003, 216.58.209.227
Connecting to www.google.fr (www.google.fr)|2a00:1450:4007:80f::2003|:80... failed: Network is unreachable.
Connecting to www.google.fr (www.google.fr)|216.58.209.227|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [text/html]
Saving to: ‘index.html’
[ <=> ] 10,495 --.-K/s in 0s
2017-03-13 23:25:02 (177 MB/s) - ‘index.html’ saved [10495]
./deploy-image-by-profile.sh pc2-101 lan101 small ubuntu1604
virsh console pc2-101
root@pc2-101:/home/user# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 52:54:00:24:ec:1d brd ff:ff:ff:ff:ff:ff
inet 192.168.168.131/24 brd 192.168.168.255 scope global ens2
valid_lft forever preferred_lft forever
inet6 fd00:168:168:0:5054:ff:fe24:ec1d/64 scope global mngtmpaddr dynamic
valid_lft 3493sec preferred_lft 3493sec
inet6 2001:db8:168:168:5054:ff:fe24:ec1d/64 scope global mngtmpaddr dynamic
valid_lft 3493sec preferred_lft 3493sec
inet6 fe80::5054:ff:fe24:ec1d/64 scope link
valid_lft forever preferred_lft forever
echo "iface ens2 inet6 dhcp" >> /etc/network/interfaces
root@pc2-101:/home/user# ip -6 a show ens2
2: ens2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 2001:db8:168:168::4a6/128 scope global
valid_lft forever preferred_lft forever
inet6 fd00:168:168::4a6/128 scope global
valid_lft forever preferred_lft forever
inet6 fd00:168:168:0:5054:ff:fe24:ec1d/64 scope global mngtmpaddr dynamic
valid_lft 3506sec preferred_lft 3506sec
inet6 2001:db8:168:168:5054:ff:fe24:ec1d/64 scope global mngtmpaddr dynamic
valid_lft 3506sec preferred_lft 3506sec
inet6 fe80::5054:ff:fe24:ec1d/64 scope link
valid_lft forever preferred_lft forever
[root@r101 ~]# cat /var/lib/dnsmasq/dnsmasq.leases
1489488084 52:54:00:24:ec:1d 192.168.168.131 pc2-101 *
1489486973 52:54:00:7b:f3:1e 192.168.168.107 pc1-101 *
duid 00:01:00:01:20:58:4e:72:52:54:00:fa:ad:5f
1489448488 2419741 2001:db8:168:168::4a6 * 00:01:00:01:20:59:dc:96:52:54:00:24:ec:1d
1489448488 2419741 fd00:168:168::4a6 * 00:01:00:01:20:59:dc:96:52:54:00:24:ec:1d
1489448956 8123166 fd00:168:168::1b4 * 00:04:f9:53:ce:4f:25:b1:c5:c5:76:5a:a9:20:35:9f:92:3a
Le fichier de configuration par défaut /etc/dnsmasq.conf est entièrement commenté sauf la dernière ligne. Il sert surtout de référence pour tous les cas possibles. On placera sa configuration dans /etc/dnsmasq.d/
On y apprend par exemple que la directive dhcp-range=fd00:1234::, ra-stateless, ra-names active la DDNS IPv6 pour les adresses autoconfigurées. Un autre exemple : la directive enable-ra impose une configuration DHCPv6 pour tous les préfixes et désactive l’autoconfiguration automatique.
Note à compléter : Avec Selinux activé, des modifications de configuration du logiciel peut nécessiter une intervention (man dnsmasq_selinux).
# Configuration file for dnsmasq.
#
# Format is one option per line, legal options are the same
# as the long options legal on the command line. See
# "/usr/sbin/dnsmasq --help" or "man 8 dnsmasq" for details.
# Listen on this specific port instead of the standard DNS port
# (53). Setting this to zero completely disables DNS function,
# leaving only DHCP and/or TFTP.
#port=5353
# The following two options make you a better netizen, since they
# tell dnsmasq to filter out queries which the public DNS cannot
# answer, and which load the servers (especially the root servers)
# unnecessarily. If you have a dial-on-demand link they also stop
# these requests from bringing up the link unnecessarily.
# Never forward plain names (without a dot or domain part)
#domain-needed
# Never forward addresses in the non-routed address spaces.
#bogus-priv
# Uncomment this to filter useless windows-originated DNS requests
# which can trigger dial-on-demand links needlessly.
# Note that (amongst other things) this blocks all SRV requests,
# so don't use it if you use eg Kerberos, SIP, XMMP or Google-talk.
# This option only affects forwarding, SRV records originating for
# dnsmasq (via srv-host= lines) are not suppressed by it.
#filterwin2k
# Change this line if you want dns to get its upstream servers from
# somewhere other that /etc/resolv.conf
#resolv-file=
# By default, dnsmasq will send queries to any of the upstream
# servers it knows about and tries to favour servers to are known
# to be up. Uncommenting this forces dnsmasq to try each query
# with each server strictly in the order they appear in
# /etc/resolv.conf
#strict-order
# If you don't want dnsmasq to read /etc/resolv.conf or any other
# file, getting its servers from this file instead (see below), then
# uncomment this.
#no-resolv
# If you don't want dnsmasq to poll /etc/resolv.conf or other resolv
# files for changes and re-read them then uncomment this.
#no-poll
# Add other name servers here, with domain specs if they are for
# non-public domains.
#server=/localnet/192.168.0.1
# Example of routing PTR queries to nameservers: this will send all
# address->name queries for 192.168.3/24 to nameserver 10.1.2.3
#server=/3.168.192.in-addr.arpa/10.1.2.3
# Add local-only domains here, queries in these domains are answered
# from /etc/hosts or DHCP only.
#local=/localnet/
# Add domains which you want to force to an IP address here.
# The example below send any host in double-click.net to a local
# web-server.
#address=/double-click.net/127.0.0.1
# --address (and --server) work with IPv6 addresses too.
#address=/www.thekelleys.org.uk/fe80::20d:60ff:fe36:f83
# Add the IPs of all queries to yahoo.com, google.com, and their
# subdomains to the vpn and search ipsets:
#ipset=/yahoo.com/google.com/vpn,search
# You can control how dnsmasq talks to a server: this forces
# queries to 10.1.2.3 to be routed via eth1
# server=10.1.2.3@eth1
# and this sets the source (ie local) address used to talk to
# 10.1.2.3 to 192.168.1.1 port 55 (there must be a interface with that
# IP on the machine, obviously).
# server=10.1.2.3@192.168.1.1#55
# If you want dnsmasq to change uid and gid to something other
# than the default, edit the following lines.
#user=
#group=
# If you want dnsmasq to listen for DHCP and DNS requests only on
# specified interfaces (and the loopback) give the name of the
# interface (eg eth0) here.
# Repeat the line for more than one interface.
#interface=
# Or you can specify which interface _not_ to listen on
#except-interface=
# Or which to listen on by address (remember to include 127.0.0.1 if
# you use this.)
#listen-address=
# If you want dnsmasq to provide only DNS service on an interface,
# configure it as shown above, and then use the following line to
# disable DHCP and TFTP on it.
#no-dhcp-interface=
# On systems which support it, dnsmasq binds the wildcard address,
# even when it is listening on only some interfaces. It then discards
# requests that it shouldn't reply to. This has the advantage of
# working even when interfaces come and go and change address. If you
# want dnsmasq to really bind only the interfaces it is listening on,
# uncomment this option. About the only time you may need this is when
# running another nameserver on the same machine.
#bind-interfaces
# If you don't want dnsmasq to read /etc/hosts, uncomment the
# following line.
#no-hosts
# or if you want it to read another file, as well as /etc/hosts, use
# this.
#addn-hosts=/etc/banner_add_hosts
# Set this (and domain: see below) if you want to have a domain
# automatically added to simple names in a hosts-file.
#expand-hosts
# Set the domain for dnsmasq. this is optional, but if it is set, it
# does the following things.
# 1) Allows DHCP hosts to have fully qualified domain names, as long
# as the domain part matches this setting.
# 2) Sets the "domain" DHCP option thereby potentially setting the
# domain of all systems configured by DHCP
# 3) Provides the domain part for "expand-hosts"
#domain=thekelleys.org.uk
# Set a different domain for a particular subnet
#domain=wireless.thekelleys.org.uk,192.168.2.0/24
# Same idea, but range rather then subnet
#domain=reserved.thekelleys.org.uk,192.68.3.100,192.168.3.200
# Uncomment this to enable the integrated DHCP server, you need
# to supply the range of addresses available for lease and optionally
# a lease time. If you have more than one network, you will need to
# repeat this for each network on which you want to supply DHCP
# service.
#dhcp-range=192.168.0.50,192.168.0.150,12h
# This is an example of a DHCP range where the netmask is given. This
# is needed for networks we reach the dnsmasq DHCP server via a relay
# agent. If you don't know what a DHCP relay agent is, you probably
# don't need to worry about this.
#dhcp-range=192.168.0.50,192.168.0.150,255.255.255.0,12h
# This is an example of a DHCP range which sets a tag, so that
# some DHCP options may be set only for this network.
#dhcp-range=set:red,192.168.0.50,192.168.0.150
# Use this DHCP range only when the tag "green" is set.
#dhcp-range=tag:green,192.168.0.50,192.168.0.150,12h
# Specify a subnet which can't be used for dynamic address allocation,
# is available for hosts with matching --dhcp-host lines. Note that
# dhcp-host declarations will be ignored unless there is a dhcp-range
# of some type for the subnet in question.
# In this case the netmask is implied (it comes from the network
# configuration on the machine running dnsmasq) it is possible to give
# an explicit netmask instead.
#dhcp-range=192.168.0.0,static
# Enable DHCPv6. Note that the prefix-length does not need to be specified
# and defaults to 64 if missing/
#dhcp-range=1234::2, 1234::500, 64, 12h
# Do Router Advertisements, BUT NOT DHCP for this subnet.
#dhcp-range=1234::, ra-only
# Do Router Advertisements, BUT NOT DHCP for this subnet, also try and
# add names to the DNS for the IPv6 address of SLAAC-configured dual-stack
# hosts. Use the DHCPv4 lease to derive the name, network segment and
# MAC address and assume that the host will also have an
# IPv6 address calculated using the SLAAC alogrithm.
#dhcp-range=1234::, ra-names
# Do Router Advertisements, BUT NOT DHCP for this subnet.
# Set the lifetime to 46 hours. (Note: minimum lifetime is 2 hours.)
#dhcp-range=1234::, ra-only, 48h
# Do DHCP and Router Advertisements for this subnet. Set the A bit in the RA
# so that clients can use SLAAC addresses as well as DHCP ones.
#dhcp-range=1234::2, 1234::500, slaac
# Do Router Advertisements and stateless DHCP for this subnet. Clients will
# not get addresses from DHCP, but they will get other configuration information.
# They will use SLAAC for addresses.
#dhcp-range=1234::, ra-stateless
# Do stateless DHCP, SLAAC, and generate DNS names for SLAAC addresses
# from DHCPv4 leases.
#dhcp-range=1234::, ra-stateless, ra-names
# Do router advertisements for all subnets where we're doing DHCPv6
# Unless overriden by ra-stateless, ra-names, et al, the router
# advertisements will have the M and O bits set, so that the clients
# get addresses and configuration from DHCPv6, and the A bit reset, so the
# clients don't use SLAAC addresses.
#enable-ra
# Supply parameters for specified hosts using DHCP. There are lots
# of valid alternatives, so we will give examples of each. Note that
# IP addresses DO NOT have to be in the range given above, they just
# need to be on the same network. The order of the parameters in these
# do not matter, it's permissible to give name, address and MAC in any
# order.
# Always allocate the host with Ethernet address 11:22:33:44:55:66
# The IP address 192.168.0.60
#dhcp-host=11:22:33:44:55:66,192.168.0.60
# Always set the name of the host with hardware address
# 11:22:33:44:55:66 to be "fred"
#dhcp-host=11:22:33:44:55:66,fred
# Always give the host with Ethernet address 11:22:33:44:55:66
# the name fred and IP address 192.168.0.60 and lease time 45 minutes
#dhcp-host=11:22:33:44:55:66,fred,192.168.0.60,45m
# Give a host with Ethernet address 11:22:33:44:55:66 or
# 12:34:56:78:90:12 the IP address 192.168.0.60. Dnsmasq will assume
# that these two Ethernet interfaces will never be in use at the same
# time, and give the IP address to the second, even if it is already
# in use by the first. Useful for laptops with wired and wireless
# addresses.
#dhcp-host=11:22:33:44:55:66,12:34:56:78:90:12,192.168.0.60
# Give the machine which says its name is "bert" IP address
# 192.168.0.70 and an infinite lease
#dhcp-host=bert,192.168.0.70,infinite
# Always give the host with client identifier 01:02:02:04
# the IP address 192.168.0.60
#dhcp-host=id:01:02:02:04,192.168.0.60
# Always give the host with client identifier "marjorie"
# the IP address 192.168.0.60
#dhcp-host=id:marjorie,192.168.0.60
# Enable the address given for "judge" in /etc/hosts
# to be given to a machine presenting the name "judge" when
# it asks for a DHCP lease.
#dhcp-host=judge
# Never offer DHCP service to a machine whose Ethernet
# address is 11:22:33:44:55:66
#dhcp-host=11:22:33:44:55:66,ignore
# Ignore any client-id presented by the machine with Ethernet
# address 11:22:33:44:55:66. This is useful to prevent a machine
# being treated differently when running under different OS's or
# between PXE boot and OS boot.
#dhcp-host=11:22:33:44:55:66,id:*
# Send extra options which are tagged as "red" to
# the machine with Ethernet address 11:22:33:44:55:66
#dhcp-host=11:22:33:44:55:66,set:red
# Send extra options which are tagged as "red" to
# any machine with Ethernet address starting 11:22:33:
#dhcp-host=11:22:33:*:*:*,set:red
# Give a fixed IPv6 address and name to client with
# DUID 00:01:00:01:16:d2:83:fc:92:d4:19:e2:d8:b2
# Note the MAC addresses CANNOT be used to identify DHCPv6 clients.
# Note also the they [] around the IPv6 address are obilgatory.
#dhcp-host=id:00:01:00:01:16:d2:83:fc:92:d4:19:e2:d8:b2, fred, [1234::5]
# Ignore any clients which are not specified in dhcp-host lines
# or /etc/ethers. Equivalent to ISC "deny unknown-clients".
# This relies on the special "known" tag which is set when
# a host is matched.
#dhcp-ignore=tag:!known
# Send extra options which are tagged as "red" to any machine whose
# DHCP vendorclass string includes the substring "Linux"
#dhcp-vendorclass=set:red,Linux
# Send extra options which are tagged as "red" to any machine one
# of whose DHCP userclass strings includes the substring "accounts"
#dhcp-userclass=set:red,accounts
# Send extra options which are tagged as "red" to any machine whose
# MAC address matches the pattern.
#dhcp-mac=set:red,00:60:8C:*:*:*
# If this line is uncommented, dnsmasq will read /etc/ethers and act
# on the ethernet-address/IP pairs found there just as if they had
# been given as --dhcp-host options. Useful if you keep
# MAC-address/host mappings there for other purposes.
#read-ethers
# Send options to hosts which ask for a DHCP lease.
# See RFC 2132 for details of available options.
# Common options can be given to dnsmasq by name:
# run "dnsmasq --help dhcp" to get a list.
# Note that all the common settings, such as netmask and
# broadcast address, DNS server and default route, are given
# sane defaults by dnsmasq. You very likely will not need
# any dhcp-options. If you use Windows clients and Samba, there
# are some options which are recommended, they are detailed at the
# end of this section.
# Override the default route supplied by dnsmasq, which assumes the
# router is the same machine as the one running dnsmasq.
#dhcp-option=3,1.2.3.4
# Do the same thing, but using the option name
#dhcp-option=option:router,1.2.3.4
# Override the default route supplied by dnsmasq and send no default
# route at all. Note that this only works for the options sent by
# default (1, 3, 6, 12, 28) the same line will send a zero-length option
# for all other option numbers.
#dhcp-option=3
# Set the NTP time server addresses to 192.168.0.4 and 10.10.0.5
#dhcp-option=option:ntp-server,192.168.0.4,10.10.0.5
# Send DHCPv6 option. Note [] around IPv6 addresses.
#dhcp-option=option6:dns-server,[1234::77],[1234::88]
# Send DHCPv6 option for namservers as the machine running
# dnsmasq and another.
#dhcp-option=option6:dns-server,[::],[1234::88]
# Ask client to poll for option changes every six hours. (RFC4242)
#dhcp-option=option6:information-refresh-time,6h
# Set the NTP time server address to be the same machine as
# is running dnsmasq
#dhcp-option=42,0.0.0.0
# Set the NIS domain name to "welly"
#dhcp-option=40,welly
# Set the default time-to-live to 50
#dhcp-option=23,50
# Set the "all subnets are local" flag
#dhcp-option=27,1
# Send the etherboot magic flag and then etherboot options (a string).
#dhcp-option=128,e4:45:74:68:00:00
#dhcp-option=129,NIC=eepro100
# Specify an option which will only be sent to the "red" network
# (see dhcp-range for the declaration of the "red" network)
# Note that the tag: part must precede the option: part.
#dhcp-option = tag:red, option:ntp-server, 192.168.1.1
# The following DHCP options set up dnsmasq in the same way as is specified
# for the ISC dhcpcd in
# http://www.samba.org/samba/ftp/docs/textdocs/DHCP-Server-Configuration.txt
# adapted for a typical dnsmasq installation where the host running
# dnsmasq is also the host running samba.
# you may want to uncomment some or all of them if you use
# Windows clients and Samba.
#dhcp-option=19,0 # option ip-forwarding off
#dhcp-option=44,0.0.0.0 # set netbios-over-TCP/IP nameserver(s) aka WINS server(s)
#dhcp-option=45,0.0.0.0 # netbios datagram distribution server
#dhcp-option=46,8 # netbios node type
# Send an empty WPAD option. This may be REQUIRED to get windows 7 to behave.
#dhcp-option=252,"\n"
# Send RFC-3397 DNS domain search DHCP option. WARNING: Your DHCP client
# probably doesn't support this......
#dhcp-option=option:domain-search,eng.apple.com,marketing.apple.com
# Send RFC-3442 classless static routes (note the netmask encoding)
#dhcp-option=121,192.168.1.0/24,1.2.3.4,10.0.0.0/8,5.6.7.8
# Send vendor-class specific options encapsulated in DHCP option 43.
# The meaning of the options is defined by the vendor-class so
# options are sent only when the client supplied vendor class
# matches the class given here. (A substring match is OK, so "MSFT"
# matches "MSFT" and "MSFT 5.0"). This example sets the
# mtftp address to 0.0.0.0 for PXEClients.
#dhcp-option=vendor:PXEClient,1,0.0.0.0
# Send microsoft-specific option to tell windows to release the DHCP lease
# when it shuts down. Note the "i" flag, to tell dnsmasq to send the
# value as a four-byte integer - that's what microsoft wants. See
# http://technet2.microsoft.com/WindowsServer/en/library/a70f1bb7-d2d4-49f0-96d6-4b7414ecfaae1033.mspx?mfr=true
#dhcp-option=vendor:MSFT,2,1i
# Send the Encapsulated-vendor-class ID needed by some configurations of
# Etherboot to allow is to recognise the DHCP server.
#dhcp-option=vendor:Etherboot,60,"Etherboot"
# Send options to PXELinux. Note that we need to send the options even
# though they don't appear in the parameter request list, so we need
# to use dhcp-option-force here.
# See http://syslinux.zytor.com/pxe.php#special for details.
# Magic number - needed before anything else is recognised
#dhcp-option-force=208,f1:00:74:7e
# Configuration file name
#dhcp-option-force=209,configs/common
# Path prefix
#dhcp-option-force=210,/tftpboot/pxelinux/files/
# Reboot time. (Note 'i' to send 32-bit value)
#dhcp-option-force=211,30i
# Set the boot filename for netboot/PXE. You will only need
# this is you want to boot machines over the network and you will need
# a TFTP server; either dnsmasq's built in TFTP server or an
# external one. (See below for how to enable the TFTP server.)
#dhcp-boot=pxelinux.0
# The same as above, but use custom tftp-server instead machine running dnsmasq
#dhcp-boot=pxelinux,server.name,192.168.1.100
# Boot for Etherboot gPXE. The idea is to send two different
# filenames, the first loads gPXE, and the second tells gPXE what to
# load. The dhcp-match sets the gpxe tag for requests from gPXE.
#dhcp-match=set:gpxe,175 # gPXE sends a 175 option.
#dhcp-boot=tag:!gpxe,undionly.kpxe
#dhcp-boot=mybootimage
# Encapsulated options for Etherboot gPXE. All the options are
# encapsulated within option 175
#dhcp-option=encap:175, 1, 5b # priority code
#dhcp-option=encap:175, 176, 1b # no-proxydhcp
#dhcp-option=encap:175, 177, string # bus-id
#dhcp-option=encap:175, 189, 1b # BIOS drive code
#dhcp-option=encap:175, 190, user # iSCSI username
#dhcp-option=encap:175, 191, pass # iSCSI password
# Test for the architecture of a netboot client. PXE clients are
# supposed to send their architecture as option 93. (See RFC 4578)
#dhcp-match=peecees, option:client-arch, 0 #x86-32
#dhcp-match=itanics, option:client-arch, 2 #IA64
#dhcp-match=hammers, option:client-arch, 6 #x86-64
#dhcp-match=mactels, option:client-arch, 7 #EFI x86-64
# Do real PXE, rather than just booting a single file, this is an
# alternative to dhcp-boot.
#pxe-prompt="What system shall I netboot?"
# or with timeout before first available action is taken:
#pxe-prompt="Press F8 for menu.", 60
# Available boot services. for PXE.
#pxe-service=x86PC, "Boot from local disk"
# Loads <tftp-root>/pxelinux.0 from dnsmasq TFTP server.
#pxe-service=x86PC, "Install Linux", pxelinux
# Loads <tftp-root>/pxelinux.0 from TFTP server at 1.2.3.4.
# Beware this fails on old PXE ROMS.
#pxe-service=x86PC, "Install Linux", pxelinux, 1.2.3.4
# Use bootserver on network, found my multicast or broadcast.
#pxe-service=x86PC, "Install windows from RIS server", 1
# Use bootserver at a known IP address.
#pxe-service=x86PC, "Install windows from RIS server", 1, 1.2.3.4
# If you have multicast-FTP available,
# information for that can be passed in a similar way using options 1
# to 5. See page 19 of
# http://download.intel.com/design/archives/wfm/downloads/pxespec.pdf
# Enable dnsmasq's built-in TFTP server
#enable-tftp
# Set the root directory for files available via FTP.
#tftp-root=/var/ftpd
# Make the TFTP server more secure: with this set, only files owned by
# the user dnsmasq is running as will be send over the net.
#tftp-secure
# This option stops dnsmasq from negotiating a larger blocksize for TFTP
# transfers. It will slow things down, but may rescue some broken TFTP
# clients.
#tftp-no-blocksize
# Set the boot file name only when the "red" tag is set.
#dhcp-boot=tag:red,pxelinux.red-net
# An example of dhcp-boot with an external TFTP server: the name and IP
# address of the server are given after the filename.
# Can fail with old PXE ROMS. Overridden by --pxe-service.
#dhcp-boot=/var/ftpd/pxelinux.0,boothost,192.168.0.3
# If there are multiple external tftp servers having a same name
# (using /etc/hosts) then that name can be specified as the
# tftp_servername (the third option to dhcp-boot) and in that
# case dnsmasq resolves this name and returns the resultant IP
# addresses in round robin fasion. This facility can be used to
# load balance the tftp load among a set of servers.
#dhcp-boot=/var/ftpd/pxelinux.0,boothost,tftp_server_name
# Set the limit on DHCP leases, the default is 150
#dhcp-lease-max=150
# The DHCP server needs somewhere on disk to keep its lease database.
# This defaults to a sane location, but if you want to change it, use
# the line below.
#dhcp-leasefile=/var/lib/dnsmasq/dnsmasq.leases
# Set the DHCP server to authoritative mode. In this mode it will barge in
# and take over the lease for any client which broadcasts on the network,
# whether it has a record of the lease or not. This avoids long timeouts
# when a machine wakes up on a new network. DO NOT enable this if there's
# the slightest chance that you might end up accidentally configuring a DHCP
# server for your campus/company accidentally. The ISC server uses
# the same option, and this URL provides more information:
# http://www.isc.org/files/auth.html
#dhcp-authoritative
# Run an executable when a DHCP lease is created or destroyed.
# The arguments sent to the script are "add" or "del",
# then the MAC address, the IP address and finally the hostname
# if there is one.
#dhcp-script=/bin/echo
# Set the cachesize here.
#cache-size=150
# If you want to disable negative caching, uncomment this.
#no-negcache
# Normally responses which come from /etc/hosts and the DHCP lease
# file have Time-To-Live set as zero, which conventionally means
# do not cache further. If you are happy to trade lower load on the
# server for potentially stale date, you can set a time-to-live (in
# seconds) here.
#local-ttl=
# If you want dnsmasq to detect attempts by Verisign to send queries
# to unregistered .com and .net hosts to its sitefinder service and
# have dnsmasq instead return the correct NXDOMAIN response, uncomment
# this line. You can add similar lines to do the same for other
# registries which have implemented wildcard A records.
#bogus-nxdomain=64.94.110.11
# If you want to fix up DNS results from upstream servers, use the
# alias option. This only works for IPv4.
# This alias makes a result of 1.2.3.4 appear as 5.6.7.8
#alias=1.2.3.4,5.6.7.8
# and this maps 1.2.3.x to 5.6.7.x
#alias=1.2.3.0,5.6.7.0,255.255.255.0
# and this maps 192.168.0.10->192.168.0.40 to 10.0.0.10->10.0.0.40
#alias=192.168.0.10-192.168.0.40,10.0.0.0,255.255.255.0
# Change these lines if you want dnsmasq to serve MX records.
# Return an MX record named "maildomain.com" with target
# servermachine.com and preference 50
#mx-host=maildomain.com,servermachine.com,50
# Set the default target for MX records created using the localmx option.
#mx-target=servermachine.com
# Return an MX record pointing to the mx-target for all local
# machines.
#localmx
# Return an MX record pointing to itself for all local machines.
#selfmx
# Change the following lines if you want dnsmasq to serve SRV
# records. These are useful if you want to serve ldap requests for
# Active Directory and other windows-originated DNS requests.
# See RFC 2782.
# You may add multiple srv-host lines.
# The fields are <name>,<target>,<port>,<priority>,<weight>
# If the domain part if missing from the name (so that is just has the
# service and protocol sections) then the domain given by the domain=
# config option is used. (Note that expand-hosts does not need to be
# set for this to work.)
# A SRV record sending LDAP for the example.com domain to
# ldapserver.example.com port 389
#srv-host=_ldap._tcp.example.com,ldapserver.example.com,389
# A SRV record sending LDAP for the example.com domain to
# ldapserver.example.com port 389 (using domain=)
#domain=example.com
#srv-host=_ldap._tcp,ldapserver.example.com,389
# Two SRV records for LDAP, each with different priorities
#srv-host=_ldap._tcp.example.com,ldapserver.example.com,389,1
#srv-host=_ldap._tcp.example.com,ldapserver.example.com,389,2
# A SRV record indicating that there is no LDAP server for the domain
# example.com
#srv-host=_ldap._tcp.example.com
# The following line shows how to make dnsmasq serve an arbitrary PTR
# record. This is useful for DNS-SD. (Note that the
# domain-name expansion done for SRV records _does_not
# occur for PTR records.)
#ptr-record=_http._tcp.dns-sd-services,"New Employee Page._http._tcp.dns-sd-services"
# Change the following lines to enable dnsmasq to serve TXT records.
# These are used for things like SPF and zeroconf. (Note that the
# domain-name expansion done for SRV records _does_not
# occur for TXT records.)
#Example SPF.
#txt-record=example.com,"v=spf1 a -all"
#Example zeroconf
#txt-record=_http._tcp.example.com,name=value,paper=A4
# Provide an alias for a "local" DNS name. Note that this _only_ works
# for targets which are names from DHCP or /etc/hosts. Give host
# "bert" another name, bertrand
#cname=bertand,bert
# For debugging purposes, log each DNS query as it passes through
# dnsmasq.
#log-queries
# Log lots of extra information about DHCP transactions.
#log-dhcp
# Include another lot of configuration options.
#conf-file=/etc/dnsmasq.more.conf
conf-dir=/etc/dnsmasq.d
4. Topologie de lab : lab201
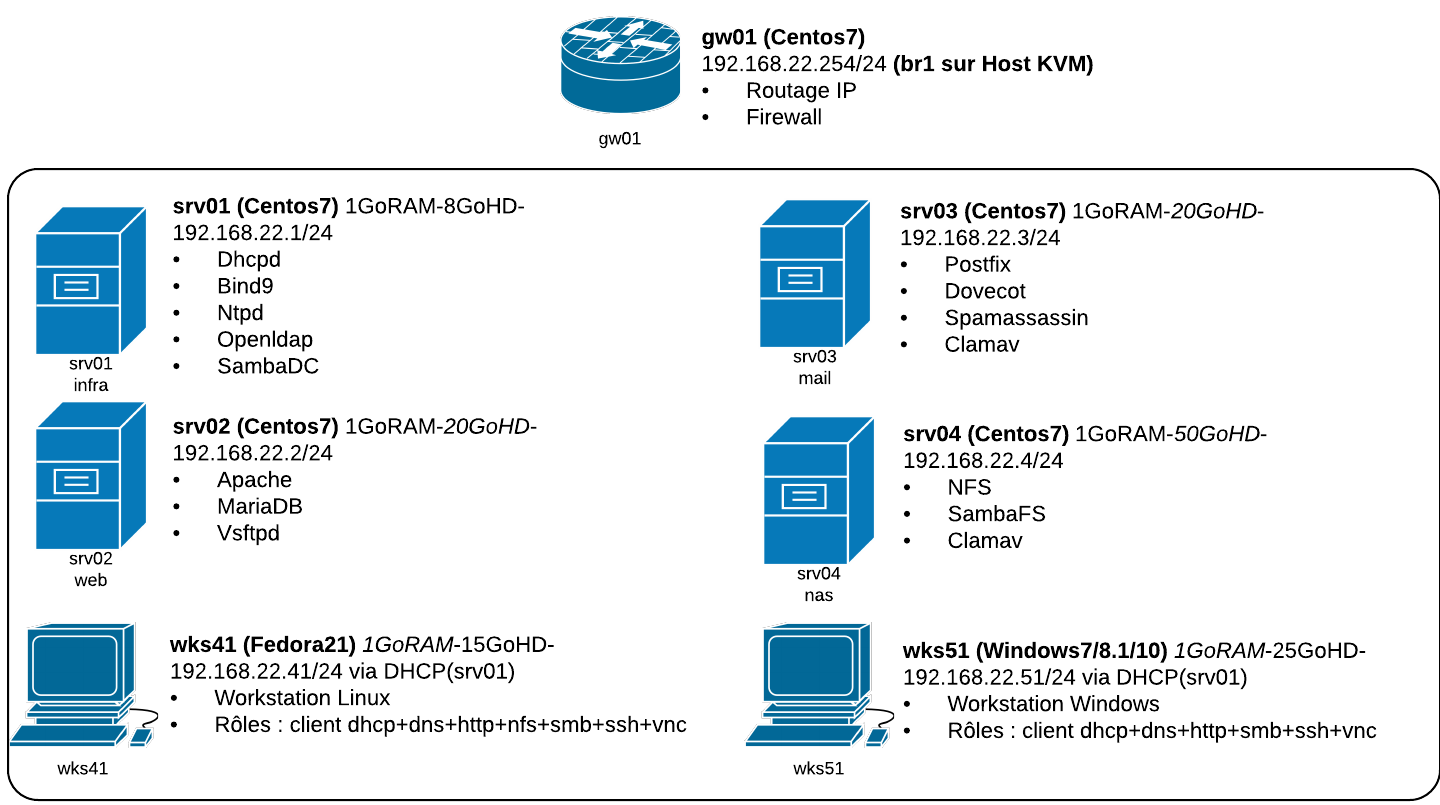
La mise en place peut se réaliser avec kcli ou avec les virt-scripts.
Déploiement avec kcli :
…
Déploiement avec “libvirt/lab201”
…
5. Mise en place de srv01
5.1. Configuration réseau
Par exemple, pour changer le nom d’hôte :
hostnamectl set-hostname srv01
systemctl restart systemd-hostnamed
systemctl status systemd-hostnamed
En changeant le nom d’hôte, on enfreint des règles SELinux.
- On peut ré-étiqueter tout le système en créant un fichier vide
.autorelabelà la racine du système et en redémarrant la machine.
# touch /.autorelabel
reboot
Modifier ou créer le fichier /etc/sysconfig/network-scripts/ifcfg-eth0 pour fixer l’adresse IP du serveur srv01 et d’autres paramètres.
DEVICE=eth0
NM_CONTROLLED=no
ONBOOT=yes
TYPE=Ethernet
BOOTPROTO=static
HOSTNAME=srv01
IPADDR=192.168.22.1
NETMASK=255.255.255.0
GATEWAY=192.168.22.254
+++ connexion IPv6
Ensuite, on éteindra la machine virtuelle afin d’éditer la définition de la VM avec virsh edit srv01 et de remplacer la ligne <source bridge='virbr0'/> par <source bridge='virbr1'/>.Après redémarrage la machine devrait obtenir une connectivité locale et globale :
- Interface
# ip addr show dev eth0
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 52:54:00:ef:72:b6 brd ff:ff:ff:ff:ff:ff
inet 192.168.22.1/24 brd 192.168.22.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::5054:ff:feef:72b6/64 scope link
valid_lft forever preferred_lft forever
- Connectivité locale
# ping -c 1 192.168.22.254
PING 192.168.22.254 (192.168.22.254) 56(84) bytes of data.
64 bytes from 192.168.22.254: icmp_seq=1 ttl=64 time=0.324 ms
--- 192.168.22.254 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.324/0.324/0.324/0.000 ms
- Connectivité globale
# ping -c 1 8.8.8.8
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
64 bytes from 8.8.8.8: icmp_seq=1 ttl=127 time=47.7 ms
--- 8.8.8.8 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 47.775/47.775/47.775/0.000 ms
- Mais la résolution de nom est absente
# ping -c 1 www.google.com
ping: unknown host www.google.com
- En effet, il n’y a pas de serveur de nom renseigné dans
/etc/resolv.confsinon la référence originale qu’il faut modfier en valeur temporairenameserver 8.8.8.8
# cat /etc/resolv.conf
# Generated by NetworkManager
nameserver 8.8.8.8
- Maintenant une connectivité minimale est établie
# ping -c 1 www.google.com
PING www.google.com (62.4.253.244) 56(84) bytes of data.
64 bytes from 244.253-4-62.akamai.com (62.4.253.244): icmp_seq=1 ttl=127 time=43.7 ms
--- www.google.com ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 43.717/43.717/43.717/0.000 ms
5.2. Service DHCP
# yum -y install dhcp
Créer un fichier /etc/dhcp/dhcpd.conf
ddns-update-style none;
authoritative;
log-facility local7;
subnet 192.168.22.0 netmask 255.255.255.0 {
range 192.168.22.100 192.168.22.150;
option domain-name-servers 192.168.22.1;
option domain-name "domain.lan";
option routers 192.168.22.254;
option ntp-servers 192.168.22.1;
default-lease-time 86400;
max-lease-time 86400;
}
#host srv02 {
# hardware ethernet aa:bb:cc:dd:ee:ff;
# fixed-address 192.168.22.2;
#}
Activation et démarrage du service
# systemctl enable dhcpd
# systemctl start dhcpd
Baux attribés
# cat /var/lib/dhcpd/dhcpd.leases
# The format of this file is documented in the dhcpd.leases(5) manual page.
# This lease file was written by isc-dhcp-4.2.5
lease 192.168.22.100 {
starts 3 2016/03/09 18:21:24;
ends 4 2016/03/10 18:21:24;
tstp 4 2016/03/10 18:21:24;
cltt 3 2016/03/09 18:21:24;
binding state active;
next binding state free;
rewind binding state free;
hardware ethernet 52:54:00:ef:05:b3;
client-hostname "wks41";
}
lease 192.168.22.101 {
starts 3 2016/03/09 18:32:01;
ends 4 2016/03/10 18:32:01;
tstp 4 2016/03/10 18:32:01;
cltt 3 2016/03/09 18:32:01;
binding state active;
next binding state free;
rewind binding state free;
hardware ethernet 52:54:00:ef:38:81;
client-hostname "srv02";
}
server-duid "\000\001\000\001\036s%\241RT\000\357r\266";
Journal Centos / Debian (pour mémoire)
journalctl -u dhcpd || journalctl -u isc-dhcp-server
5.3. DNS
Une lecture de ce document https://access.redhat.com/documentation/fr-FR/Red_Hat_Enterprise_Linux/7/html/Networking_Guide/ch-DNS_Servers.html en français expose les principes de configuration de Bind9.
Installation de Bind9
yum -y install bind bind-utils
Configuration cache DNS
Editer le fichier /etc/named.conf
- Création d’une ACL
- Mise à l’écoute sur le LAN
- Ajout des Forwarders
# cat /etc/named.conf
//
// named.conf
//
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS
// server as a caching only nameserver (as a localhost DNS resolver only).
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
// Les ajouts sont indiqué //!!!
//!!! Création d'une ACL "trusted"
acl trusted {
192.168.22.0/24; localhost;
};
options {
//!!! Mise à l'écoute sur l'adresse 192.168.122.1
listen-on port 53 { 127.0.0.1; 192.168.22.1; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
//!!! Autoriser les requêtes correspondant à l'ACL "trusted"
allow-query { trusted; };
/*
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes;
dnssec-enable yes;
dnssec-validation yes;
/* Path to ISC DLV key */
bindkeys-file "/etc/named.iscdlv.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
//!!! Ajouter des serveurs de noms publics (exemple)
forwarders { 8.8.8.8; 8.8.4.4; };
};
logging
{
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
Activation et démarrage du service DNS
# systemctl enable named
# systemctl start named
# systemctl status named
Toute opération future nécessite un redémarrage du démon named :
rndc reload
Ajout des paramètres locaux tels quels dans /etc/resolv.conf
# echo "domain domain.lan" > /etc/resolv.conf
# echo "search domain.lan" >> /etc/resolv.conf
# echo "nameserver 127.0.0.1" >> /etc/resolv.conf
# cat /etc/resolv.conf
domain domain.lan
search domain.lan
nameserver 127.0.0.1
Mais aussi une mise-à-jour du fichier de résolution locale /etc/hosts semble indiquée.
# echo "127.0.0.1 srv01 srv01.domain.lan" >> /etc/hosts
# echo "::1 srv01 srv01.domain.lan" >> /etc/hosts
# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
127.0.0.1 srv01 srv01.domain.lan
::1 srv01 srv01.domain.lan
Diagnostic
# ss -antp | grep named
LISTEN 0 10 192.168.22.1:53 *:* use
rs:(("named",pid=8864,fd=21))
LISTEN 0 10 127.0.0.1:53 *:* users:
(("named",pid=8864,fd=20))
LISTEN 0 128 127.0.0.1:953 *:* users:
(("named",pid=8864,fd=23))
LISTEN 0 10 ::1:53 :::* users:((
"named",pid=8864,fd=22))
LISTEN 0 128 ::1:953 :::* users:((
"named",pid=8864,fd=24))
# journalctl -e -u named
# dig +short @127.0.0.1 www.google.com
216.58.211.100
# dig +short @192.168.22.1 www.google.com
216.58.211.100
named-checkconf
named-checkzone [zone] [zone file path]
Test à partir de wks41
[root@wks41 ~]# nslookup www.google.com
Server: 192.168.22.1
Address: 192.168.22.1#53
Non-authoritative answer:
Name: www.google.com
Address: 216.58.211.68
Hébergement d’une zone locale
Déclaration des fichiers de zone. On ajoutera ces lignes à la fin du fichier /etc/named.conf
zone "domain.lan" {
type master;
file "db.domain.lan";
#allow-update { key rndc-key; };
};
zone "22.168.192.in-addr.arpa" {
type master;
file "db.192.168.22";
#allow-update { key rndc-key; };
};
Ajout des fichiers de zone
Editer un nouveau fichier /var/named/db.domain.lan
$TTL 604800
@ IN SOA srv01.domain.lan. francois.domain.lan. (
1 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
@ IN NS srv01.domain.lan.
srv01 IN A 192.168.22.1
ns1 IN CNAME srv01
gw01 IN A 192.168.1.254
Editer un nouveau fichier/var/named/db.192.168.22
$TTL 604800
@ IN SOA srv01.domain.lan. francois.domain.lan. (
1 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
@ IN NS srv01.
1 IN PTR srv01.domain.lan.
254 IN PTR gw01.domain.lan
Fixer les droits
# chown named:named /var/named/db*
# ls -l /var/named/db*
-rw-r--r--. 1 named named 447 Mar 9 20:28 /var/named/db.192.168.22
-rw-r--r--. 1 named named 472 Mar 9 20:26 /var/named/db.domain.lan
Redémarrage du service
# systemctl restart named
Vérification de la configuration des zones
# named-checkconf -z
zone localhost.localdomain/IN: loaded serial 0
zone localhost/IN: loaded serial 0
zone 1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa/IN: loaded serial 0
zone 1.0.0.127.in-addr.arpa/IN: loaded serial 0
zone 0.in-addr.arpa/IN: loaded serial 0
zone domain.lan/IN: loaded serial 1
zone 22.168.192.in-addr.arpa/IN: loaded serial 1
Tests locaux et distants avec dig srv01.domain.lan
Chaque fois qu’un fichier de zone connaît un changement, il faut incrémenter la valeur de champ serial.
5.4. Chroot Bind
Sans SELinux, un environnement chroot pour Bind est peut-être recommandé.
# yum install -y bind-chroot
# /usr/libexec/setup-named-chroot.sh /var/named/chroot on
# systemctl disable named
# systemctl stop named
# systemctl enable named-chroot
Created symlink from /etc/systemd/system/multi-user.target.wants/named-chroot.service to /usr/lib/systemd/system/named-chroot.service.
# systemctl start named-chroot
# yum install -y tree
# tree /var/named/chroot/
/var/named/chroot/
├── dev
│ ├── null
│ ├── random
│ └── zero
├── etc
│ ├── localtime
│ ├── named
│ ├── named.conf
│ ├── named.iscdlv.key
│ ├── named.rfc1912.zones
│ ├── named.root.key
│ ├── pki
│ │ └── dnssec-keys
│ └── rndc.key
├── run
│ └── named
│ ├── named.pid
│ └── session.key
├── usr
│ └── lib64
│ └── bind
└── var
├── log
├── named
│ ├── chroot
│ │ ├── dev
│ │ │ ├── null
│ │ │ ├── random
│ │ │ └── zero
│ │ ├── etc
│ │ │ ├── localtime
│ │ │ ├── named
│ │ │ ├── named.conf
│ │ │ ├── named.iscdlv.key
│ │ │ ├── named.rfc1912.zones
│ │ │ ├── named.root.key
│ │ │ ├── pki
│ │ │ │ └── dnssec-keys
│ │ │ └── rndc.key
│ │ ├── run
│ │ │ └── named
│ │ ├── usr
│ │ │ └── lib64
│ │ │ └── bind
│ │ └── var
│ │ ├── log
│ │ ├── named
│ │ ├── run -> ../run
│ │ └── tmp
│ ├── data
│ │ └── named.run
│ ├── dynamic
│ │ ├── managed-keys.bind
│ │ └── managed-keys.bind.jnl
│ ├── named.ca
│ ├── named.empty
│ ├── named.localhost
│ ├── named.loopback
│ └── slaves
├── run -> ../run
└── tmp
34 directories, 27 files
[root@00 ~]#
5.5. DHCP/DNS dynamique
- Nom : srv01.domain.lan
- Type : Authoritative
- Forward Lookup Zone : domain.lan.
- Reverse Lookup Zone : 22.168.192.in-addr.arpa.
Il faut adapter le fichier /etc/named.conf avec la clé d’authentification “rndc-key”
//
// named.conf
//
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS
// server as a caching only nameserver (as a localhost DNS resolver only).
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
// Les ajouts sont indiqué //!!!
//!!! Création d'une ACL "lan"
acl trusted {
192.168.22.0/24; localhost;
};
options {
//!!! Mise à l'écoute sur l'adresse 192.168.122.1
listen-on port 53 { 127.0.0.1; 192.168.22.1; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
//!!! Autoriser les requêtes correspondant à l'ACL "trusted"
allow-query { trusted; };
/*
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes;
dnssec-enable yes;
dnssec-validation yes;
/* Path to ISC DLV key */
bindkeys-file "/etc/named.iscdlv.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
//!!! Ajouter des serveurs de noms publics (exemple)
forwarders { 8.8.8.8; 8.8.4.4; };
//!!! restrict recursion
allow-recursion {
trusted;
};
allow-transfer {
trusted;
};
};
logging
{
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
//!!! adapté
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
zone "domain.lan" {
type master;
file "db.domain.lan";
allow-update { key rndc-key; };
};
zone "22.168.192.in-addr.arpa" {
type master;
file "db.192.168.22";
allow-update { key rndc-key; };
};
//!!! Ajouté
include "/etc/rndc.key";
Mais quelle est cette clé ? Chacun aura la sienne. Notez la bien.
# cat /etc/rndc.key
key "rndc-key" {
algorithm hmac-md5;
secret "QD54SMYw8Zpthvk1e6oAoA==";
};
# ls -l /etc/rndc.key
-rw-r-----. 1 root named 77 Mar 9 19:55 /etc/rndc.key
SELinux interdit l’écriture dynamique des fichiers de zones
Configurer SELinux en conséquence
setsebool named_write_master_zones true
On va renseigner directement cette clé dans le fichier /etc/dhcp/dhcpd.conf ici adapté
Faisons-en une sauvegarde et adaptons le fichier :
cp /etc/dhcp/dhcpd.conf ~/dhcpd.conf.bak
# cat /etc/dhcp/dhcpd.conf
#
# DHCP Server Configuration file.
# see /usr/share/doc/dhcp*/dhcpd.conf.example
# see dhcpd.conf(5) man page
#
ddns-updates on;
ddns-update-style interim;
key "rndc-key" {
algorithm hmac-md5;
secret "QD54SMYw8Zpthvk1e6oAoA==";
};
#ddns-update-style none;
authoritative;
log-facility local7;
subnet 192.168.22.0 netmask 255.255.255.0 {
range 192.168.22.100 192.168.22.150;
option domain-name-servers 192.168.22.1;
option domain-name "domain.lan";
option routers 192.168.22.254;
option ntp-servers 192.168.22.1;
default-lease-time 86400;
max-lease-time 86400;
}
zone domain.lan {
primary srv01;
key rndc-key;
}
zone 22.168.192.in-addr.arpa {
primary srv01;
key rndc-key;
}
Fixer le propriétaire et le groupe named sur le répertoire /var/named et redémarrer les deux services
# chown -R named:named /var/named/
# systemctl restart named && systemctl restart dhcpd
Après avoir redémarré wks41, vérifier sa résolution de nom
dig wks41
5.6. NTP côté Serveur
Srv01 est aussi serveur NTP pour le réseau. NTP est un service qu’il faudrait dupliquer et qui devrait disposer de sa propre entrée dans la zone. Une idée serait de disposer d’un nom round robin qui distribuerait la charge des synchronisation sur plusieurs serveurs.
Fixer et vérifier la zone horaire
# timedatectl set-timezone Europe/Brussels
# timedatectl
Installer et activer ntpd local
# yum -y install ntp
# systemctl enable ntpd
# systemctl start ntpd
Examiner le fichier de configuration
# cat /etc/ntp
ntp/ ntp.conf
[root@localhost user]# cat /etc/ntp.conf
# For more information about this file, see the man pages
# ntp.conf(5), ntp_acc(5), ntp_auth(5), ntp_clock(5), ntp_misc(5), ntp_mon(5).
driftfile /var/lib/ntp/drift
# Permit time synchronization with our time source, but do not
# permit the source to query or modify the service on this system.
restrict default nomodify notrap nopeer noquery
# Permit all access over the loopback interface. This could
# be tightened as well, but to do so would effect some of
# the administrative functions.
restrict 127.0.0.1
restrict ::1
# Hosts on local network are less restricted.
#restrict 192.168.1.0 mask 255.255.255.0 nomodify notrap
# Use public servers from the pool.ntp.org project.
# Please consider joining the pool (http://www.pool.ntp.org/join.html).
server 0.centos.pool.ntp.org iburst
server 1.centos.pool.ntp.org iburst
server 2.centos.pool.ntp.org iburst
server 3.centos.pool.ntp.org iburst
#broadcast 192.168.1.255 autokey # broadcast server
#broadcastclient # broadcast client
#broadcast 224.0.1.1 autokey # multicast server
#multicastclient 224.0.1.1 # multicast client
#manycastserver 239.255.254.254 # manycast server
#manycastclient 239.255.254.254 autokey # manycast client
# Enable public key cryptography.
#crypto
includefile /etc/ntp/crypto/pw
# Key file containing the keys and key identifiers used when operating
# with symmetric key cryptography.
keys /etc/ntp/keys
# Specify the key identifiers which are trusted.
#trustedkey 4 8 42
# Specify the key identifier to use with the ntpdc utility.
#requestkey 8
# Specify the key identifier to use with the ntpq utility.
#controlkey 8
# Enable writing of statistics records.
#statistics clockstats cryptostats loopstats peerstats
# Disable the monitoring facility to prevent amplification attacks using ntpdc
# monlist command when default restrict does not include the noquery flag. See
# CVE-2013-5211 for more details.
# Note: Monitoring will not be disabled with the limited restriction flag.
disable monitor
Ce fichier /etc/ntp.conf devrait être adapté pour accepter des synchronisations du réseau local et sur les serveurs maîtres :
server 0.be.pool.ntp.org iburst
server 1.be.pool.ntp.org iburst
server 2.be.pool.ntp.org iburst
server 3.be.pool.ntp.org iburst
restrict 192.168.22.0 mask 255.255.255.0 nomodify notrap
Statut NTP
# ntpq -p
Mise-à-jour forcée
# systemctl stop ntpd
# ntpdate -u 0.be.pool.ntp.org
# systemctl start ntpd
5.7. NTP côté client
Du côté client, pour wks41 par exemple dans notre topologie, il est peut-être judicieux d’activer le démon chrony qui se synchronisera notamment sur srv01.
# yum -y install chrony
# cat /etc/chrony.conf
# systemctl enable chronyd
# systemctl start chronyd
# chronyc tracking
# chronyc sources -v
5.8. Configuration du pare-feu
Firewalld :
# for i in dhcp dns ntp; do firewall-cmd --permanent --add-service $i; done
Iptables :
…
